Improved Cross-Environment Secret Management & More
The Console has been updated with new features and UX improvements to make managing secrets across environments easier and more intuitive. We've also shipped several performance optimizations, bugfixes, and improved secret handling for self-hosted users.
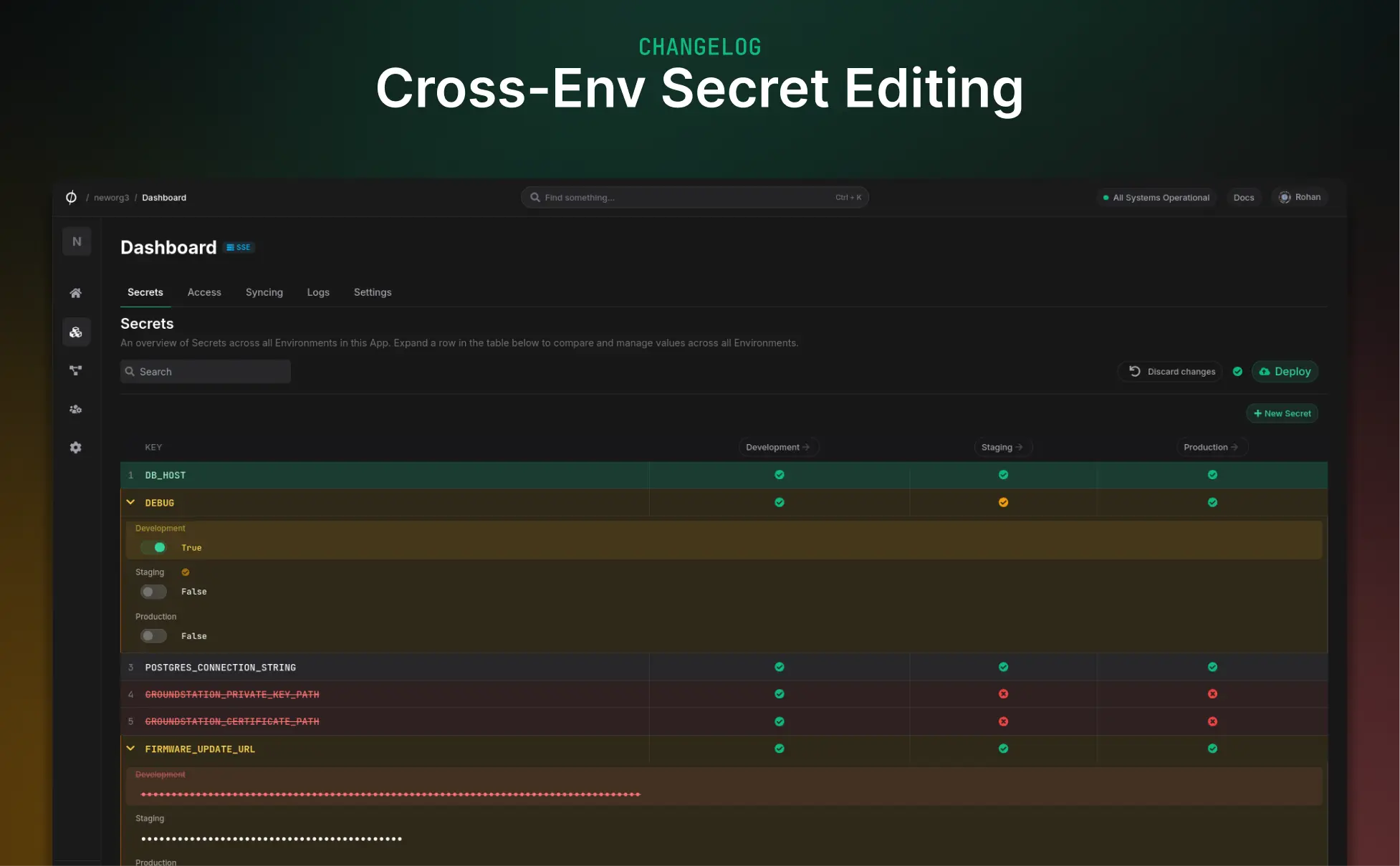
Manage Secrets Across Environments
We've heard many requests to make it easier to manage secrets across environments. Until now, each Environment in a Phase App was its own silo, and updating values for a key across multiple environments was a cumbersome process requiring many clicks and route changes. We've made the first step in a series of updates meant to improve this experience and make the workflow more intuitive for developers.
The App Secrets tab now allows you to edit secret keys and values across all environments in your App from a single screen. You can create a new secret here, which will automatically add it across all your environments. Supply a value for each environment as required, or delete a value for an environment if needed. This makes it far easier to maintain consistency across environments and reduces the need to hop between screens.
You can similarly edit secret keys and values for existing secrets across environments, delete values in an environment, or add missing values. Deleting a secret in all environments can also be done with a single click.
Deployed changes will automatically trigger sync jobs for the affected environments.
This is only the first step in improving the developer experience and workflow for managing secrets. The next few updates will focus on making it easier to clone or inherit entire environments, or just specific keys and values.
Under the hood, we've also rewritten the entire App Secrets screen to be more performant and put less load on both your browser and the backend.
Improved CLI WebAuth
We've made important updates to the authentication flow for Phase CLI users. These improvements aim to make the experience more consistent, efficient, and user-friendly.
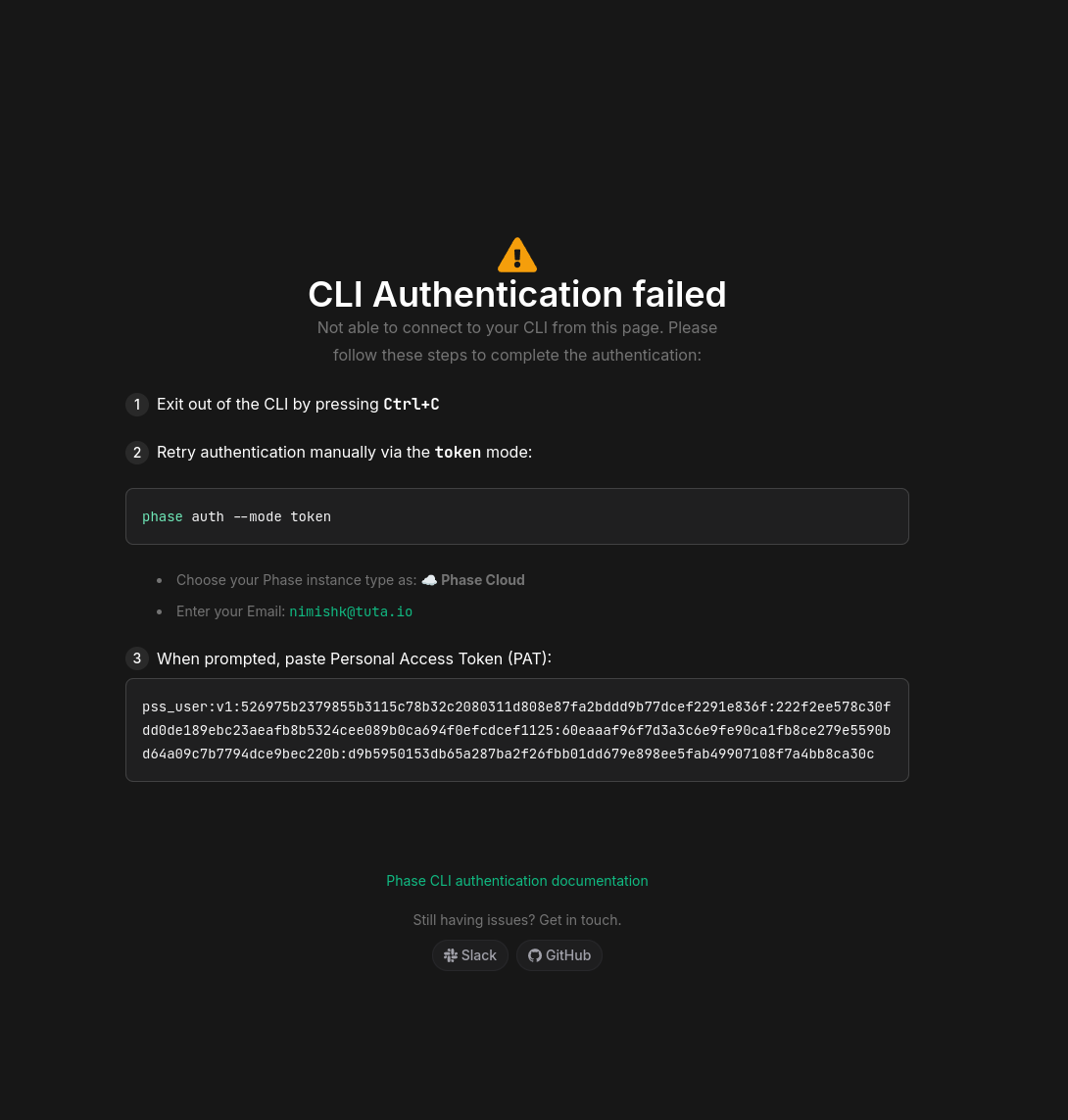
When an authentication attempt fails, users now receive clearer, step-by-step instructions to help them fall back to token-based authentication.
Here's how it looks on Phase Cloud:
and on self-hosted instances:
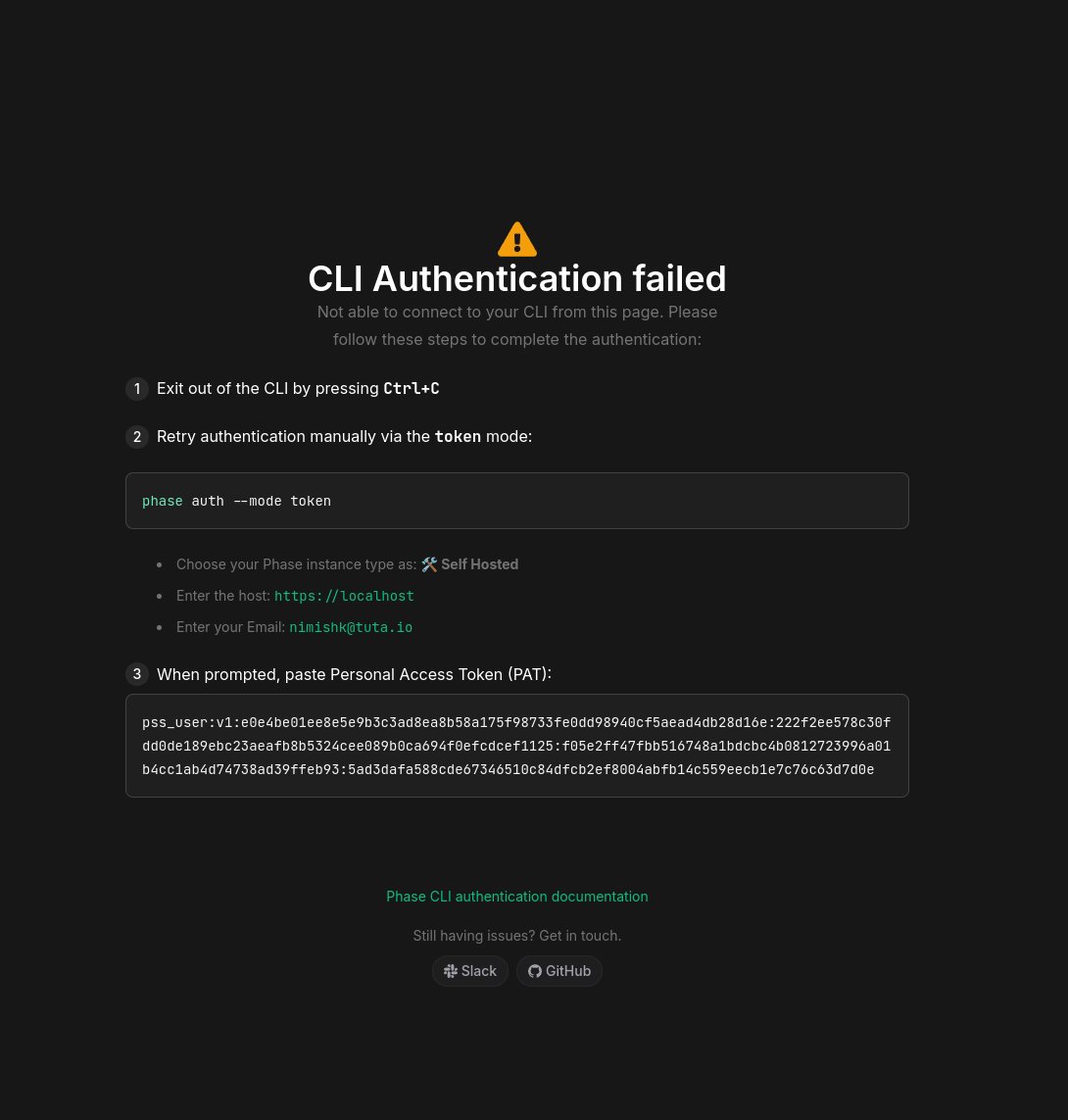
This update is part of a series of improvements we've been making to refine the CLI's authentication experience.
Key Improvements
- Enhanced Error State UI: Updated error state UI includes a numbered, step-by-step guide for troubleshooting failed authentication attempts.
- Separate Flows for Environments: Error handling now provides tailored guidance depending on whether you're using Phase Cloud or a self-hosted environment.
- Copyable Fields: Added copyable fields containing email and host details to make it easier to paste these into your terminal when going through a manual authentication flow.
- Consistent Styling: New error messages follow our design system, ensuring consistency across the CLI interface.
- Direct Links to Documentation: When users encounter issues, they can easily find additional help through direct links to relevant sections of the CLI documentation.
Performance Improvements
We've optimized network and rendering performance in key areas of the Secrets editor UI. First, we've deferred fetching of secret history data until it's required. This significantly reduces the network payload required to load the Secrets editor UI, as well as the browser resources required to decrypt and hold secret history data in memory.
Second, we've improved how this screen polls the backend for updated secrets. Polling is now skipped when your tab or window is not in view, saving unnecessary network calls and browser load, while improving overall server performance by reducing load from idle tabs.
You should notice these changes as a generally faster-loading and more responsive experience, with lower overall resource usage on your machines.
Filesystem Secrets Support
We've added support for Docker-style file-based secrets and environment variables. This enhancement streamlines the handling of sensitive configurations across Phase Console, particularly benefiting secrets and database credentials.
The implementation follows a consistent pattern across both stacks:
- Check if
{key}_FILEexists as an environment variable (e.g.,DATABASE_PASSWORD=/run/secrets/database_password) - If present, read the secret from the specified file location
- Otherwise, fall back to reading directly from environment variables
You can check out the docs for instructions on setting this up for your self-hosted instances. If you're curious about learning more about the benefits of this approach, we wrote a detailed blog post about it as well!
Cross-environment support along with all the new features and updates are live on Phase Cloud and v2.36.2 for self-hosted users.
Reach out on Slack or GitHub for any questions or feedback on this release!