Phase vs AWS Secrets Manager
AWS Secrets Manager provides powerful application secrets management tools, but is difficult to work with, lacks integrations to third party services you may be using and locks you into a single cloud provider. Phase is an open-source, end-to-end encrypted and self-hostable platform that integrates with third-party services like CI tools and hosting providers, and works with your entire team through all stages of software development.
TL;DR
Phase is for you if:
- 🧭 Usability: You desire a security solution that's laser focused on developer experience with straightforward documentation.
- 🔌 Integrations: You want a single source of truth of all your secrets that integrates with other services you may be using like GitHub, Vercel, Cloudflare etc. including AWS Secrets Manager.
- 🚀 Velocity: Time to production really matters to you. You don't want to get bogged down by unneeded complexity of AWS services.
- 👨💻 Shift left: You want security tools in the hands of developers that cover the entire application development lifecycle. 💻-> 🔨-> 📦-> ⚙️ -> ☁️.
- 🙌 Open source: You prefer an open source, self-hostable platform that you are not locked in to.
AWS Secrets manager is for you if:
- 🏗️ Ecosystem: You prefer to work with a single cloud provider.
- 👷 AWS Ops You have significant AWS expertise and want to manage secrets on behalf of developers after an application is deployed.
- 🔌 Integrations: You care about native integration to other AWS products and services eg. Cloudformation, RDS, Lambda etc.
Feature comparison
Category
Description
Solution
Open source
Yes. View on GitHub
No, AWS Secrets Manager and other related services are closed source and proprietary.
- Using open-source solutions for security tools is an industry-wide best practice.
- Open source code can be reviewed and audited by thousands of security researchers and developers for vulnerabilities — something that is not possible when a product is closed source.
- Given the developer centric nature of secret management tools users have an overview of the product roadmap and can have direct input into product development with open source solution.
Hosting options
Cloud - Get started
Self hosted - Docs
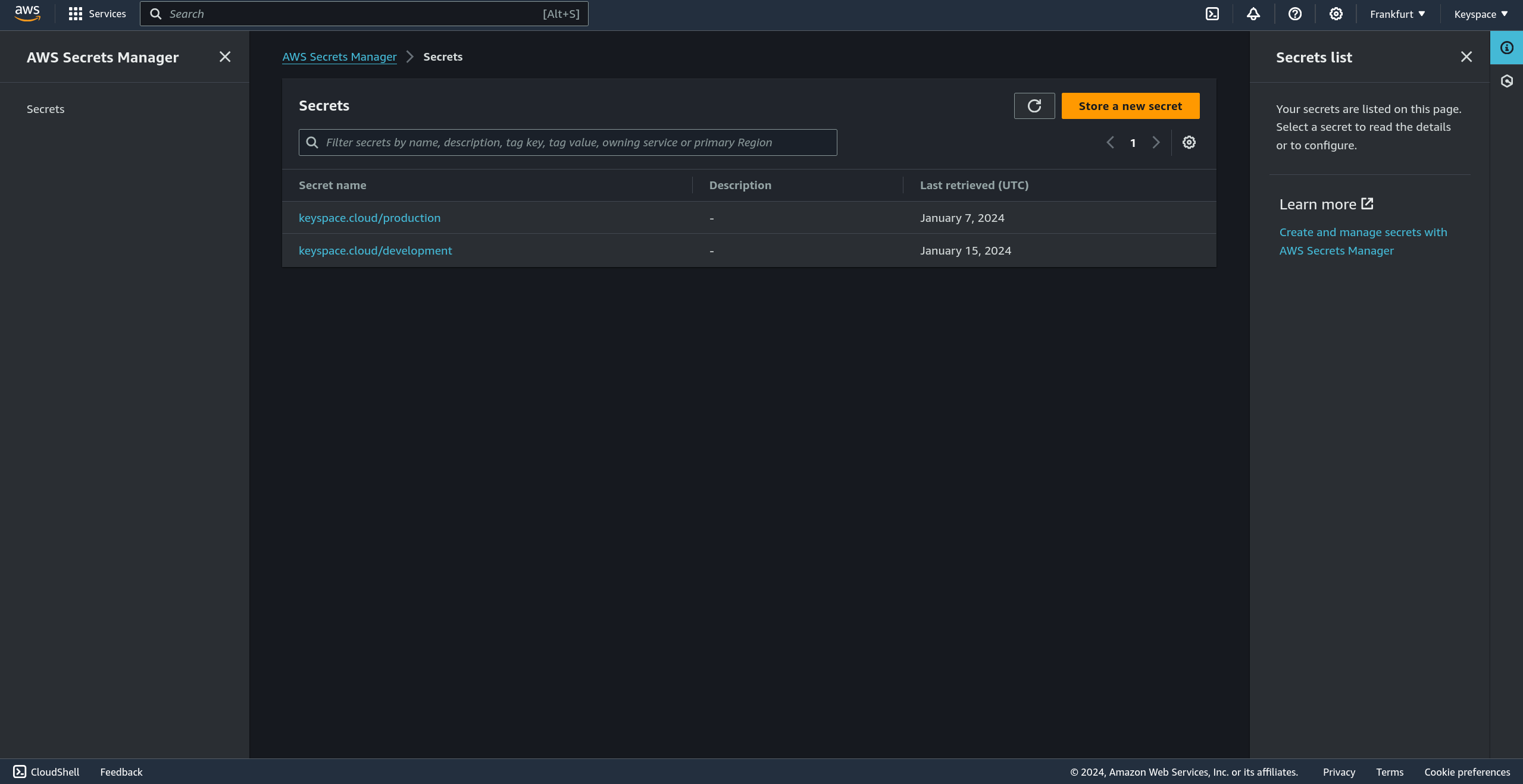
Cloud - Only on AWS
Self hosted / Multi cloud - Not available
- Phase can be self-hosted on any cloud or on your own infrastructure, eliminating vendor lock-in and improving your company's compliance posture.
- Having the option of using a cloud-hosted product is also very important if your team doesn't have the capacity to think about hosting a product themselves.
Security
Zero-knowledge Architecture
Yes. Secrets (keys, values) and secret related data such as comments and secret versions are end-to-end encrypted with keys that are generated client side on your machines. Private keys are split into two shards to avoid a single point of compromise.
No. AWS Secrets Manager sends transmits secrets in plain text over TLS and encrypts them server side with keys that under AWS's control.
Zero-knowledge Architecture leverages client side end-to-end encryption to ensure that service providers don't have access to customer keys in plain text. Using TLS only ensures that secrets are encrypted at transport, but still makes them visible to databases and backend applications. One can verify this by opening a browsers network tab in developer tools and looking at the HTTP requests or responses.
Encrypted Secret Storage
Phase uses TLS to secure data in transit as well as XChaCha-Poly1305 with keys you own to secure sensitive data at rest.
Keys are encrypted in transit with TLS and at rest with server side AES-256 encryption.
Encrypted secret storage is important to make sure that your data stays safe even when a secret management system may be compromised.
Generate secure keys / secrets
Yes. The following secrets generation types are supported: Alphanumeric, Hex, Base64, Base64 URL safe, key128, key256.
AWS Secrets Manager supports generating a random password via the AWS CLI.
Generating cryptographically secure random keys for symmetric and asymmetric encryption is critical for ensuring data security and integrity.
Self custody of keys
Yes. Phase is designed to enable self custody of keys. Only you have access to the root keys via a 24 world mnemonic phrase recovery.
No. While AWS Secrets Manager support BYOK (Bring your own keys), the custody of your encryption keys is outsourced to the AWS KMS service.
Centralized services holding customer keys are a large target for attackers. Having sole access to root keys reduces your attack surface, decentralizes risk and eliminates the need to trust third parties.
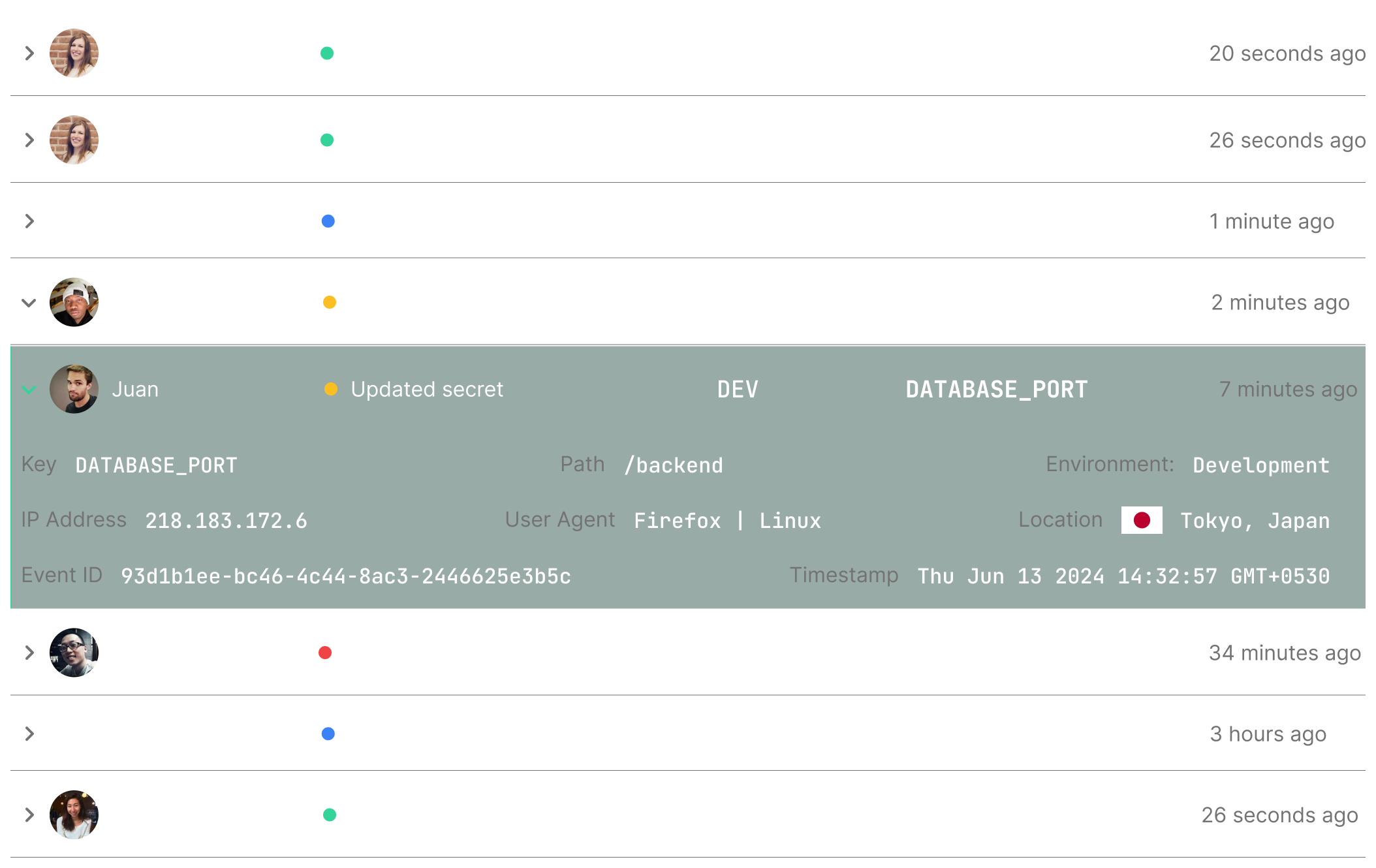
Secret access and audit logs
Yes, set up automatically out of the box, no configuration required and included for free as part of all pricing tiers.
Yes, but requires configuration with CloudTrail and CloudWatch which are billed separately.
Visibility into usage and monitoring access is critical for making sure secrets only being used by authorized parties.
Automated Secret rotation
Planned feature - will be live early Q1 2025.
Yes, but only rotations of static secrets is possible. Requires a user to set up their own lambda function.
Secret rotation are necessary to recover from incidinces of key leakage or compromise.
Filtering access to secrets via IP addresses
Yes, it is possible to filter access to secrets in an application, environments, or path to specific IPv4 and IPv6 addresses or ranges.
Yes, it is possible to filter access to a certain secret in aws secrets manager via a source IP addresses or range by using a custom IAM user policy.
Being able to restrict access to secrets for certain whitelisted IP address is an important security feature.
Developer experience
Documentation
Simple and straight forward documentation, with guides and quickstarts for multiple languages and frameworks.
Complex documentation with significant prior knowledge required of both security concepts as well as the AWS ecosystem.
Good documentation helps developers quickly and effectively implement the solution into their products, and helps them with standard patterns and best-practices.
Multi environment setup
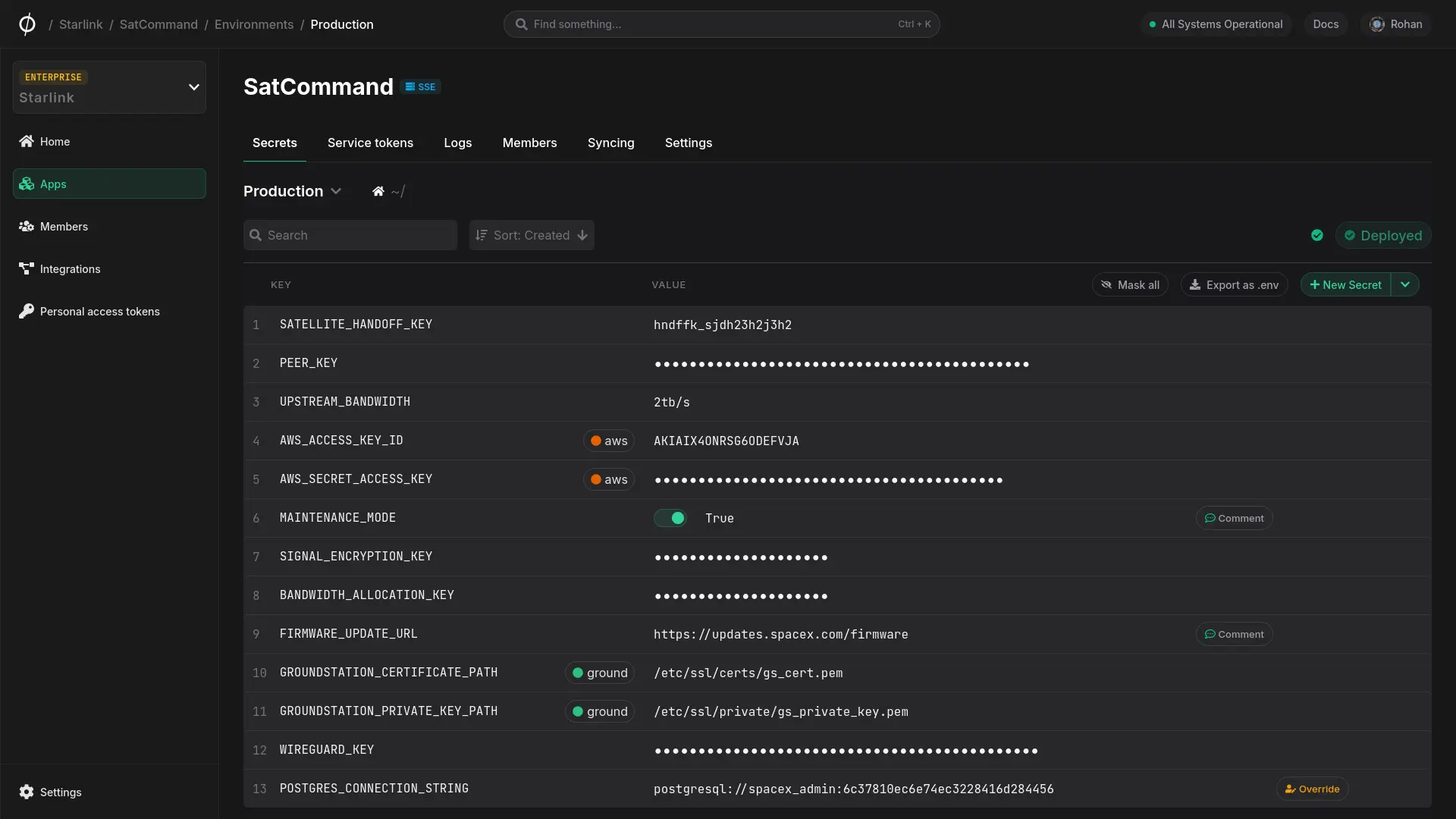
Yes. Phase automatically creates environments like development, staging and production for each of your applications out of the box.
While multiple environments can be created for your application on the AWS Secrets Manager, it requires manual setup.
Maintaining segregation between different environments eg. dev, stag, prod is important for security.
Secret deployment
Yes. Phase automatically deploys your encrypted secrets to the closest region to where your app is running to ensure low latency. No need to manually set up multiple regions.
AWS Secrets Manager requires configuring key types, regions, which can be complex due to the intricacies of AWS services and systems.
Effective deployment of secrets saves time, minimizes human error, and speeds up your application deployment.
Pricing
Simple and predictable pricing model. Phase offers a generous free tier that will along with Pro and Enterprise tiers. Pricing is primarily based on number of users.
Cost estimation can be complex as it depends on a number of variables such as number of secrets, number of requests made, multi region replication, type of key used from AWS KMS, CloudWatch logging costs.
A predictable pricing model helps estimate the cost of adoption, and makes it easier to manage your organization's security budget.
One click secret restoration
You can view the state of a secret since inception and restore to a previous value.
While viewing the previous state of a secret is possible in AWS Secrets Manager, restoring to previous versions requires you to retrieve the previous value of a secret via the VersionId and update it manually.
Being able to quickly restore a secret that was accidentally changed allows you to "Ctrl-Z" and restore your application state in a single click, preventing potential bugs, secret leaks or accidental downtime.
Secret diffs
Yes, you can compare a previous state of a secret in a git-styled diff by viewing secret history.
No
Being able to see differences between current and previous versions of a secret that has gone though multiple changes lets you easily visualize changes and provides context to all members of the team.
Point-in-time Recovery
Yes.
No
Being able to recover a key that was deleted is a critical feature to prevent accidental downtime or application errors.
Integrations - Frameworks
Yes, Phase cli can inject secrets into your application at runtime without any code changes or additional dependencies.
No
Being able to securely inject secrets into any application without the need for dependencies or code changes allows developers to integrate secret management into their workflow, and makes the solution extremely versatile.
Integrations - Secret sync
Yes, Phase can sync secrets to third party platforms and services like GitHub, Cloudflare, Vercel and AWS Secrets Manager itself.
No
Being able to securely sync secrets to other platforms and services you may be using is critical. It automates manual secret deployment and saves time.
SDKs
Yes. Phase currently has native SDKs for Golang, Python and Node.js.
Yes. AWS currently has larger support for other languages such as .NET, Java and C.
SDKs enable easy integration with your application stack.
